Programming:Unlocking ASIC
To unlock the ASIC, a 17-byte "unlock" sequence must be sent to the CRTC's selection port (&BC00) : RQ00, 0, 255, 119, 179, 81, 168, 212, 98, 57, 156, 70, 43, 21, 138, STATE, <ACQ>
- RQ00 must be different from the value 0.
- STATE=205 for UNLOCK otherwise another value for LOCK.
- ACQ represents sending any value if STATE=205 (not needed otherwise).
Note: the ASIC is already unlocked after the STATE phase, before ACQ. So ACQ is actually never needed.
Once the ASIC is unlocked, we get access to a new Gate Array register called RMR2. It is accessible in the same way as other Gate Array registers.
Contents
[hide]BASIC version
10 RESTORE 20 FOR x=0 TO 16:READ a:OUT &BC00,a:NEXT 30 DATA 255,0,255,119,179,81,168,212,98,57,156,70,43,21,138,205,238 40 PRINT"ASIC unlocked!"
Z80 Assembler version
;; This example shows how to unlock the ASIC ;; ;; This example is designed for CPC+ only and will ;; not work on CPC or KC Compact. ;; ;; This example will compile with the MAXAM assembler ;; or the built-in assembler of WinAPE32. org &8000 ;;-------------------------------------------------- ;; Unlock CPC+ additional features di ld b,&bc ld hl,sequence ld e,17 .seq ld a,(hl) out (c),a inc hl dec e jr nz,seq ei ret ;;---------------------------------------------------------- ;; this is the sequence to unlock the ASIC extra features .sequence defb &ff,&00,&ff,&77,&b3,&51,&a8,&d4,&62,&39,&9c,&46,&2b,&15,&8a,&cd,&ee
Optimized versions
The unlocking sequence can be reconstituted from simple bit operations instead of being stored in memory.
Madram version
It still uses some magic numbers.
di ld bc,#BCFF out (c),c out (c),0 ld hl,%1001000011101010 loop: out (c),c ld a,h:rlca:ld h,l:ld l,a srl c xor c:and #88:xor c ld c,a cp #4D jr nz,loop ld a,#CD ; a = #CD for unlock, another value for lock out (c),a:out (c),a ei ret
Urusergi version
No magic numbers here.
di ; v3.0 -> 30 bytes! ld bc,#BCFF out (c),c out (c),0 ld a,c loop: out (c),a ld h,a ; h = 7654 3210 add hl,hl ; h = 6543 210* rra ; a = 7765 4321 add hl,hl ; h = 5432 10** xor h:and #F7:xor h ; a = 7765 1321 add hl,hl ; h = 4321 0*** ld l,a ; l = 7765 1321 ld a,h ; a = 4321 0*** and #88:xor l ; a = (7 xor 4)765 (1 xor 0)321 cp c jr nz,loop ei ret
Algorithm
def unlock_asic():
b, c = 0xBC, 0xFF
out(b, c)
out(b, 0)
a = c
while True:
out(b, a)
# a = (7 xor 4)765 (1 xor 0)321
a = ((a >> 1) & 0x77) | ((a ^ (a << 3)) & 0x80) | (((a << 2) ^ (a << 3)) & 0x08)
if a == c: break
def out(port, value):
print(f"Port: {hex(port)}xx Out: {hex(value)}")
unlock_asic()
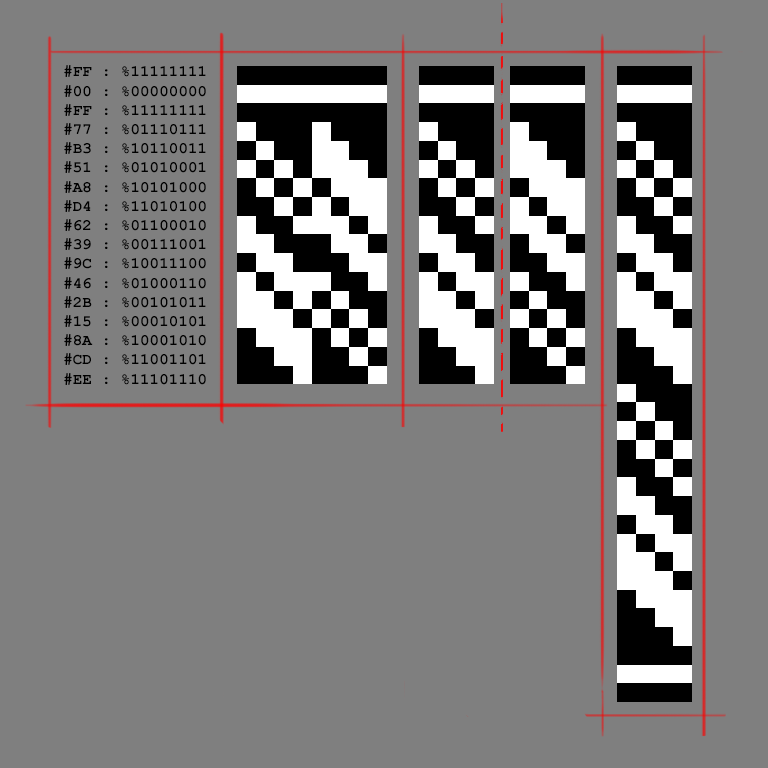
Visual representation
As one may see, the nybbles in the sequence are based on two 4bit shift registers.
Visual by Hwikaa
Patent
For one reason or another, Amstrad has patented the verification mechanism (GB2243701A).
The patent seems to focus on verifying (rather than on sending) the sequence, so its legal use is a bit unclear.
On the Original Arnold V Specs - Issue 1.5 - 10th April 1990, it is precised at §2.11 "Locking of enhanced features":
it should be noted that unauthorised use of this mechanism may infringe Amstrad's patent.